With automated user management, your users and groups in your identity provider (like OneLogin or Okta) are synchronized with New Relic.
How groups work
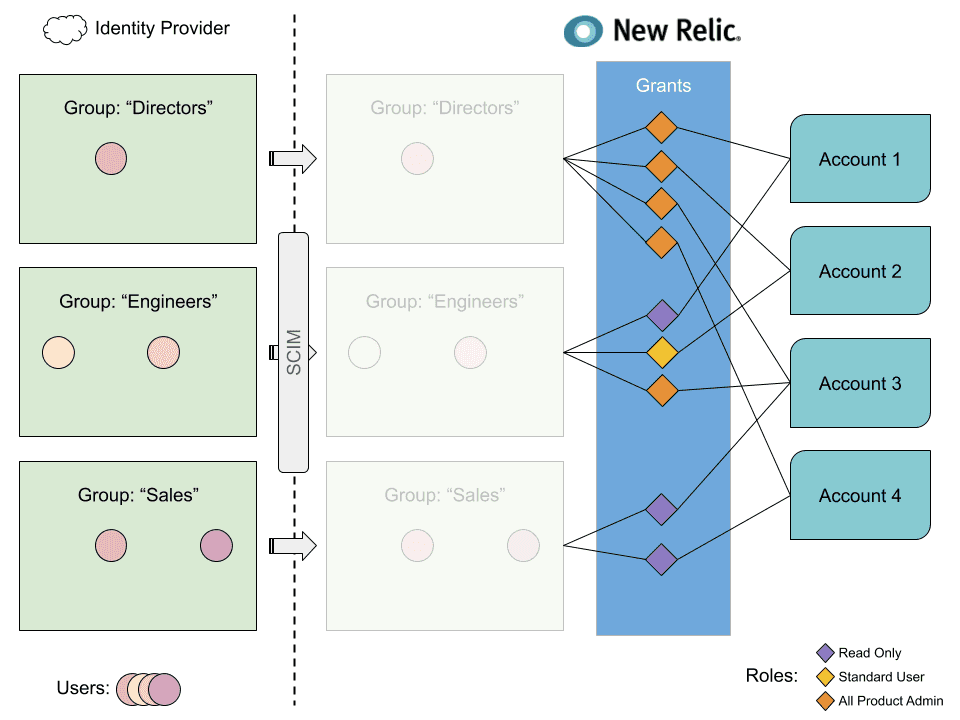
When using automated user management, you create groups of users in your identity provider service. Later, on the New Relic side, you'll create access grants, which essentially state "Give this group access to this New Relic role on this New Relic account."
An example of how the user groups in your identity provider might map over to access grants in New Relic, which assign a group access to a specific role (default or customer) on a specific account.
In the above example, let’s focus on the Engineers group. Via SCIM, New Relic will receive the two user records as well as the information that they belong to the Engineers group. In this example, the configuration would be: the two Engineer users have the Read only role on Account 1, the Standard user role on Account 2, and the All product admin role on Account 3.
This access is given by creating three access grants in New Relic:
- Access grant assigning the role Read only to the group Engineers on Account 1
- Access grant assigning the role Standard user to the group Engineers on Account 2
- Access grant assigning the role All product admin to the group Engineers on Account 3
To learn more about how access grants work, see User management concepts.
For tutorials on creating new groups and custom roles, see User management tutorials.